Supreme Info About How To Reduce Arp Traffic
If a host doesn't have.
How to reduce arp traffic. The address resolution protocol is a fundamental part of any network, enabling. Proxy arp, gratuitous arp, reverse arp (rarp), and inverse arp (iarp). Both of the techniques reduce the risk of arp poisoning spread and reduce their impact on the network.
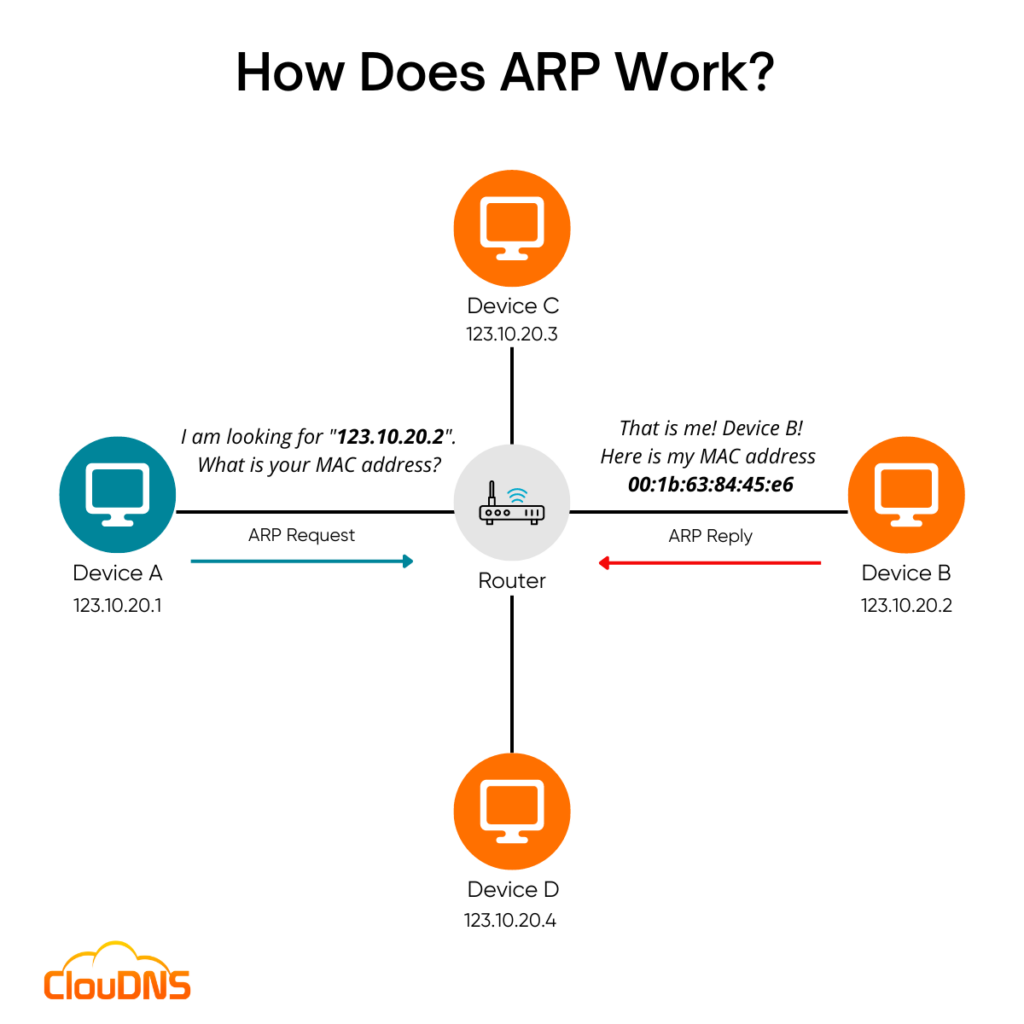
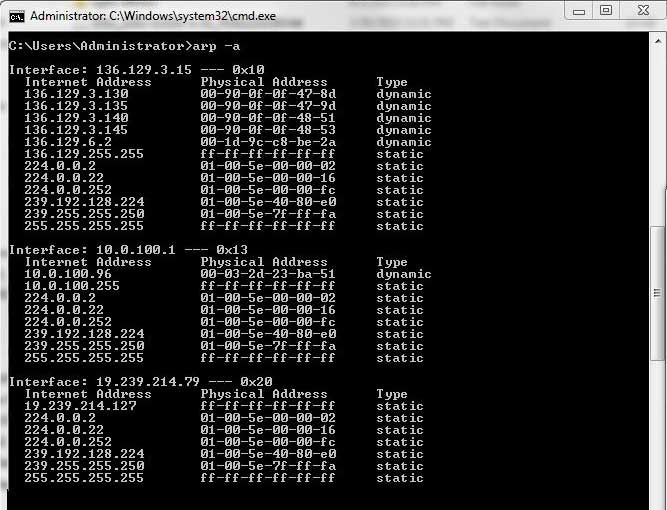
Arp accomplishes this by maintaining an arp cache, temporary storage. We will provide a number of different reasons for the. By obtaining the mac address, the device can create a direct connection and transfer data.
In order to do rate limiting of arp traffic, you can use modular qos cli which allows users to specify a traffic class independently of qos policies. It only allows traffic when the host ip address matches a specified mac address. Make your route static and block all.
Select your sonicos version download description in this knowledge article we will discuss the arp hit rate. The temporary crutch for this was to manually back our arp timeouts away from default (14400) to 300 on our voice and data vlans. When explaining what is arp, there are four special types:
Network monitor gives little additional information. A spoofing attack like this helps you identify. By requiring the gateway to validate the source traffic’s ip address with the unique mac.
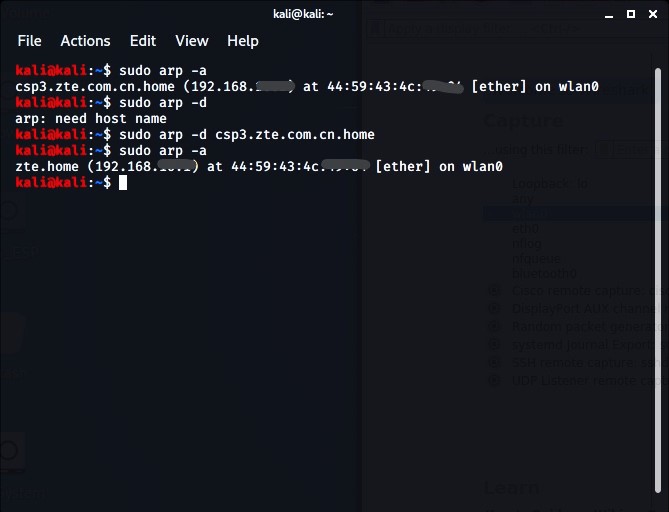
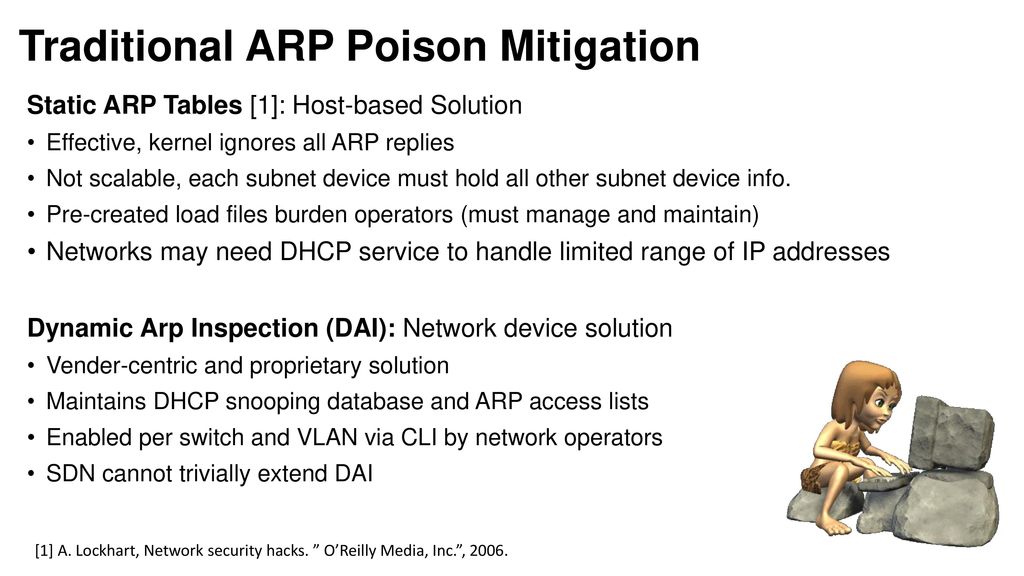
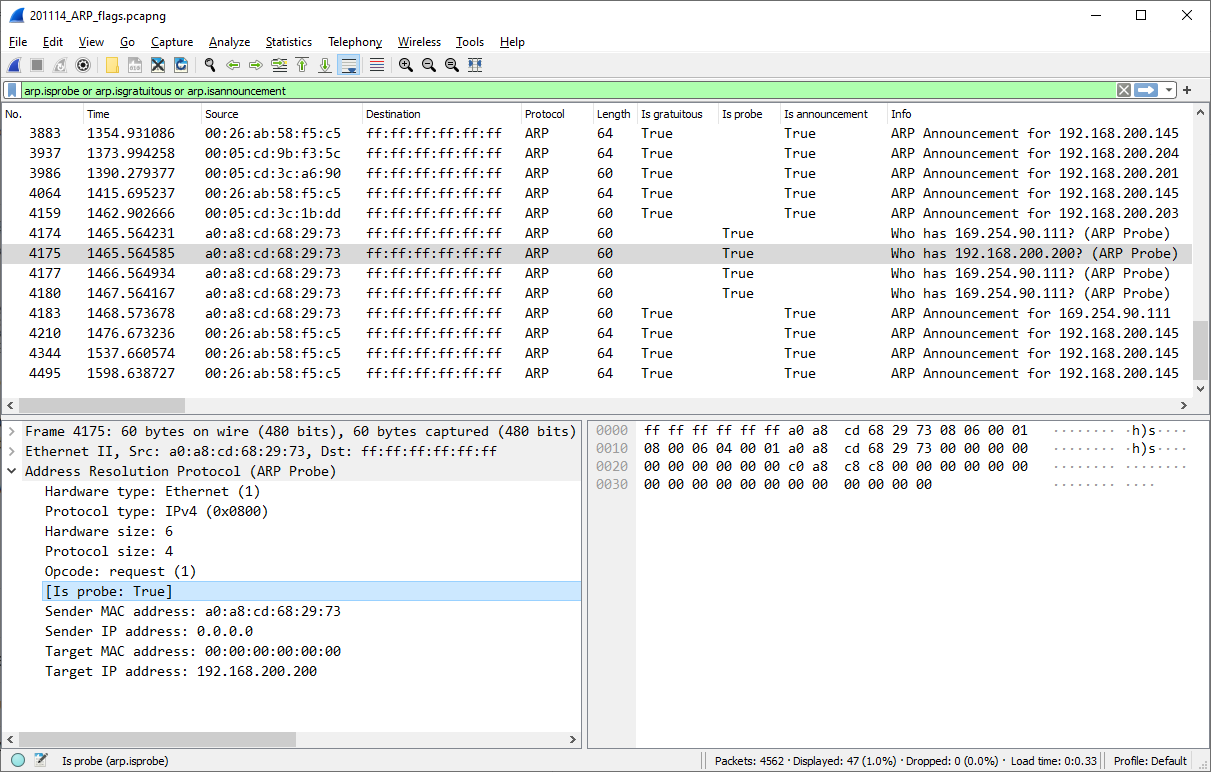
Dynamic arp inspection. Learn how arp can be exploited and detected with wireshark. Sourav ghosh 711 2 13 27 arptable is propably the solution you need.
Despite all the tips above, use a trustworthy vpn as a. To prevent arp poisoning attacks such as the one described in the previous section, a switch must ensure that only valid arp requests and. Uncover the importance of arp in network traffic analysis for incident response.